Security Checklist for systems on Amazon Web Services
Security has always been a business concern when moving to the cloud, especially for businesses that store user data such as banking, finance, real estate, and insurance. Therefore, VTI Cloud will share our cloud security checklist for systems on Amazon
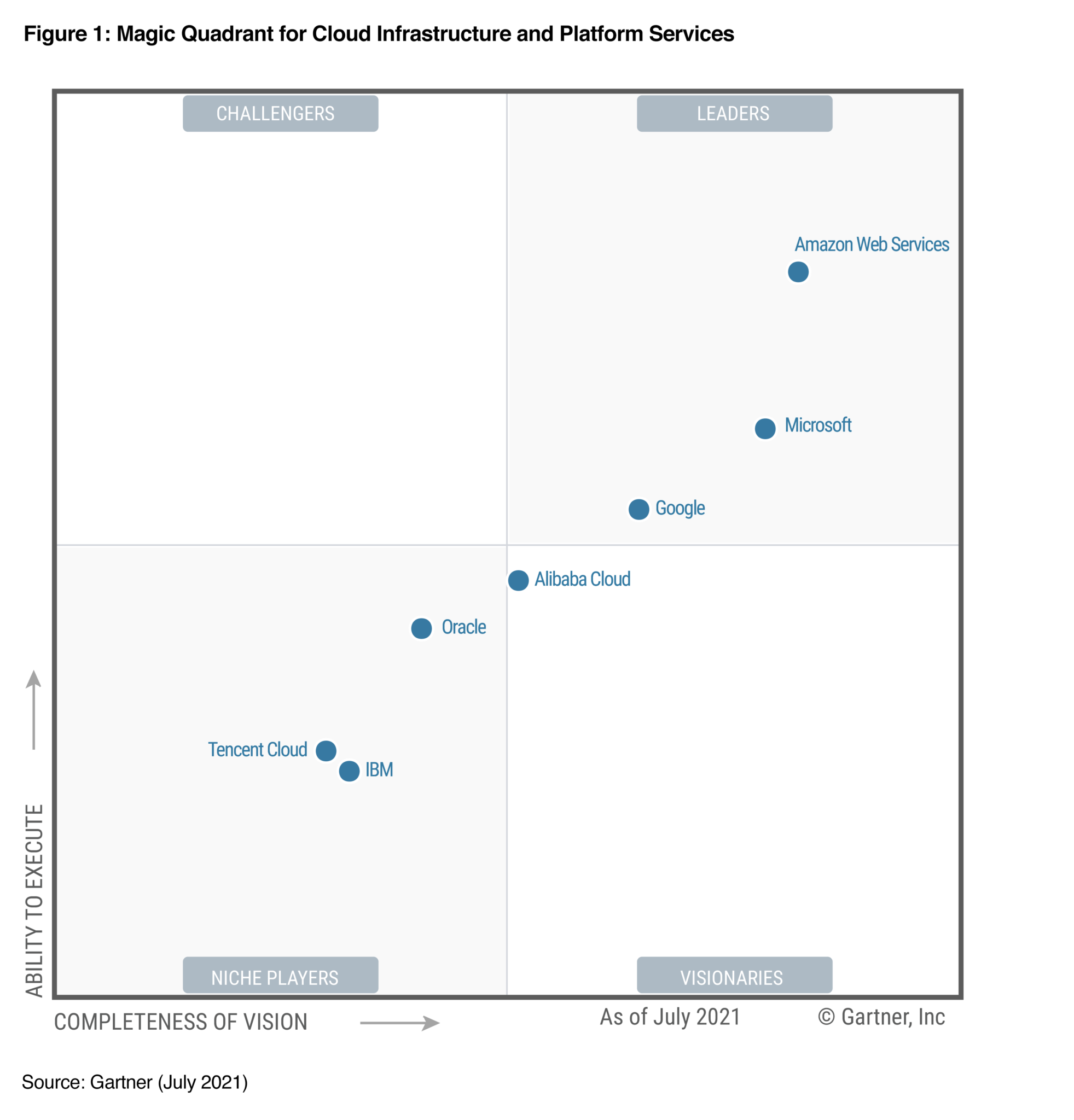
Gartner Names AWS a 2021 Magic Quadrant Leader
Gartner Names AWS a 2021 Magic Quadrant Leader Last year Gartner introduced a new Magic Quadrant for Cloud Infrastructure and Platform Services (CIPS), expanding the scope of their Magic Quadrant for Cloud Infrastructure as a Service (IaaS) to include additional platform
Cloud computing in 2021 accelerates business transformation after the COVID pandemic – Forrester predicts
“Who is really at the forefront of the digital transformation of your business: CEO, CTO or COVID?”
Understanding VPC links in Amazon API Gateway private integrations
This post is written by Jose Eduardo Montilla Lugo, Security Consultant, AWS.
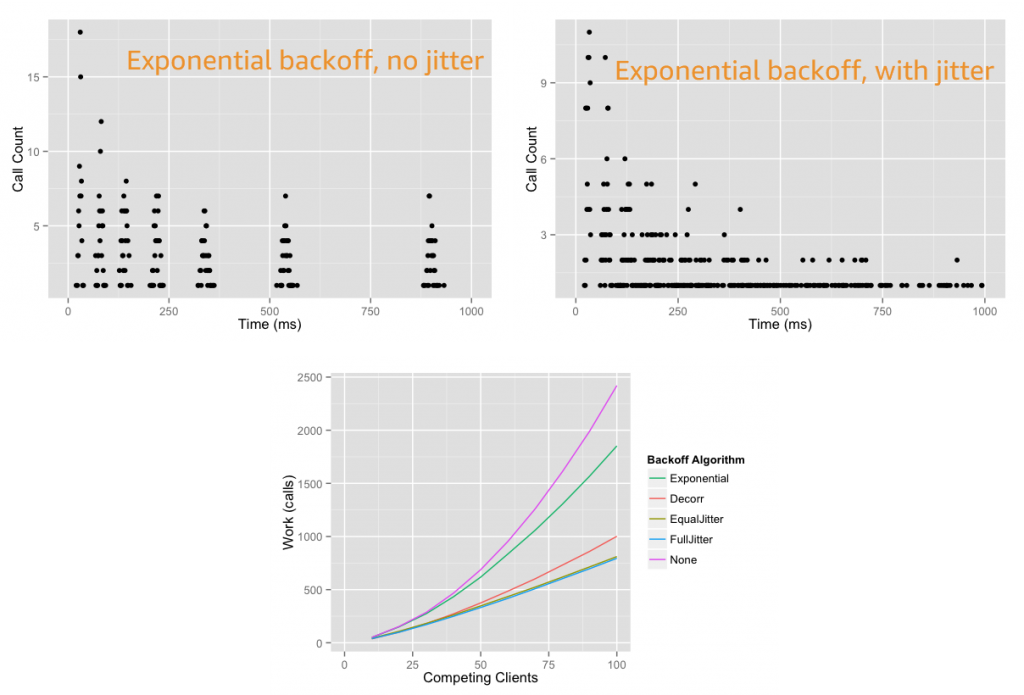
Building well-architected serverless applications: Building in resiliency – part 2
This series of blog posts uses the AWS Well-Architected Tool with the Serverless Lens to help customers build and operate applications using best practices. In each post, I address the serverless-specific questions identified by the Serverless
Building well-architected serverless applications: Building in resiliency – part 1
This series of blog posts uses the AWS Well-Architected Tool with the Serverless Lens to help customers build and operate applications using best practices. In each post, I address the serverless-specific questions identified by the Serverless
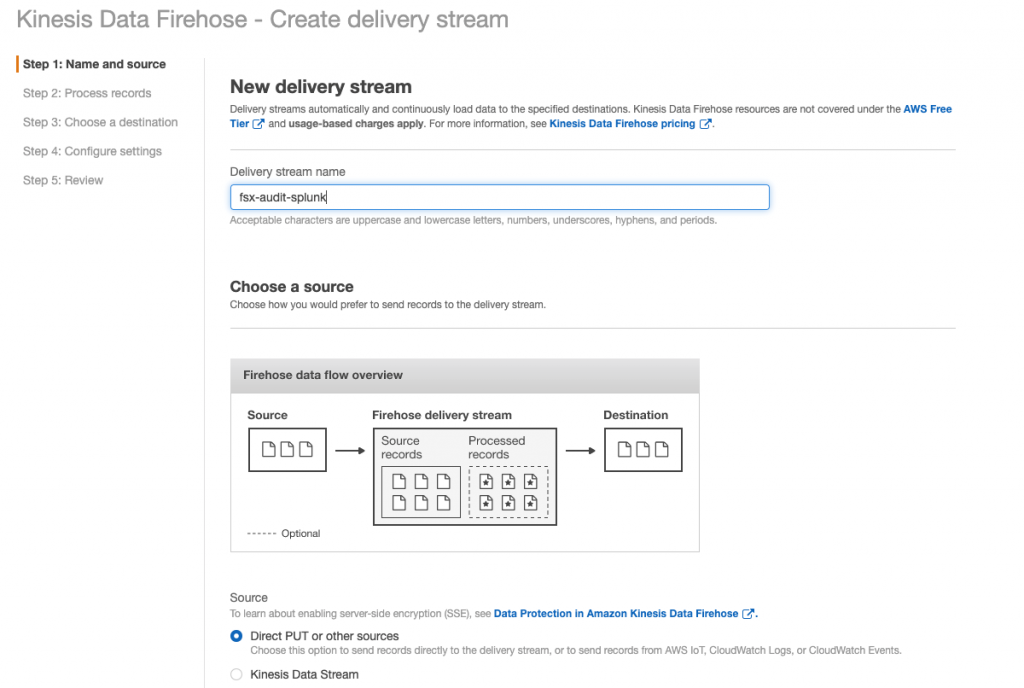
Monitoring and reporting Amazon FSx user access events using Splunk
Monitoring end-user activity and access to data is core to any modern data security strategy. As customers migrate workloads to the cloud, logging end-user accesses of customer data is a key component of internal security policies and is required to
Accessing CloudEndure Disaster Recovery with Okta single sign-on
Many organizations use single sign-on (SSO) to ensure security and compliance, streamline access management, and improve their user experience. Some organizations require all corporate applications, workloads, and solutions to use SSO for authentication, including their disaster recovery (DR) solution.