Accessing CloudEndure Disaster Recovery with Okta single sign-on
You can integrate CloudEndure Disaster Recovery, offered by AWS, into your identity provider’s (IdP) SSO using the SAML 2.0 protocol. By doing so, you can use CloudEndure Disaster Recovery to protect resources and workloads in an organization that requires SSO, and users in such an organization can securely and swiftly access their DR solution. Step-by-step details on configuring SSO for Microsoft Active Directory Federated Services (ADFS) are provided in the CloudEndure documentation.
CloudEndure Disaster Recovery shifts your DR strategy to the AWS Cloud from physical or virtual data centers, private clouds, or other public clouds. In this blog post, we provide detailed steps on how to set up SSO SAML authentication for CloudEndure Disaster Recovery using Okta as the IdP. The steps include:
- Creating the CloudEndure application in Okta.
- Configuring the SAML integration of CloudEndure application in Okta.
- Generating the IdP certificate.
- Configuring CloudEndure to use SAML.
- Adding users to Okta and CloudEndure for access.
Configuring Okta
To get started, log in to your Okta account. If you do not have an Okta account, you can create an Okta 30-day trial.
Complete the registration process and log into the Okta account. Enter the admin console by selecting the Admin button on the top right. You will be asked to enter the MFA token if configured during the setup phase.
- Once you are logged into the admin console, choose Applications under the Applications menu.
- Select Add Application.
- Next, select Create New App.
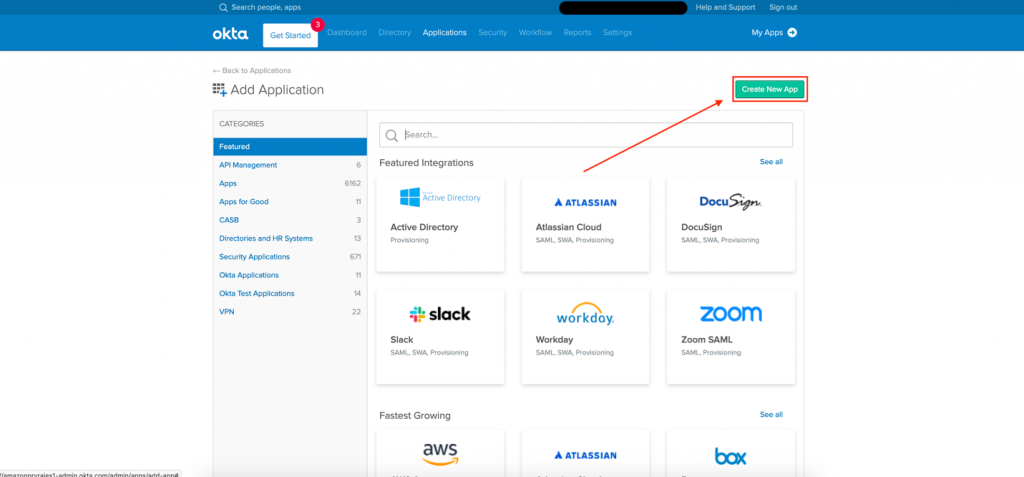
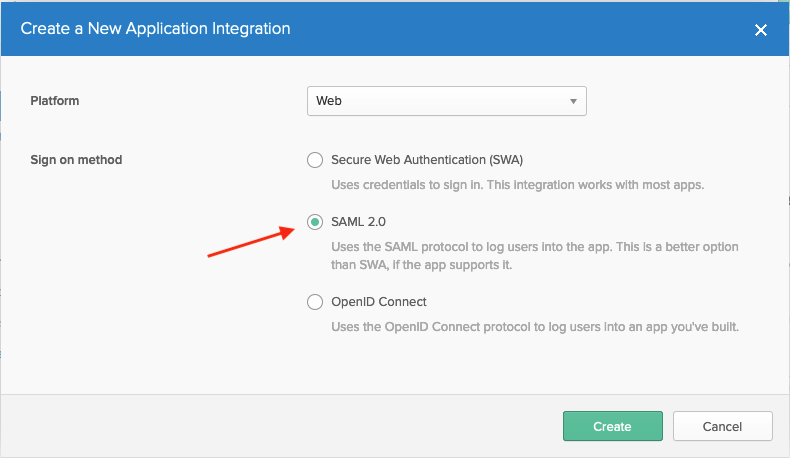
- Choose Web as the Platform and Sign on method as SAML 2.0. Afterward, select Create.
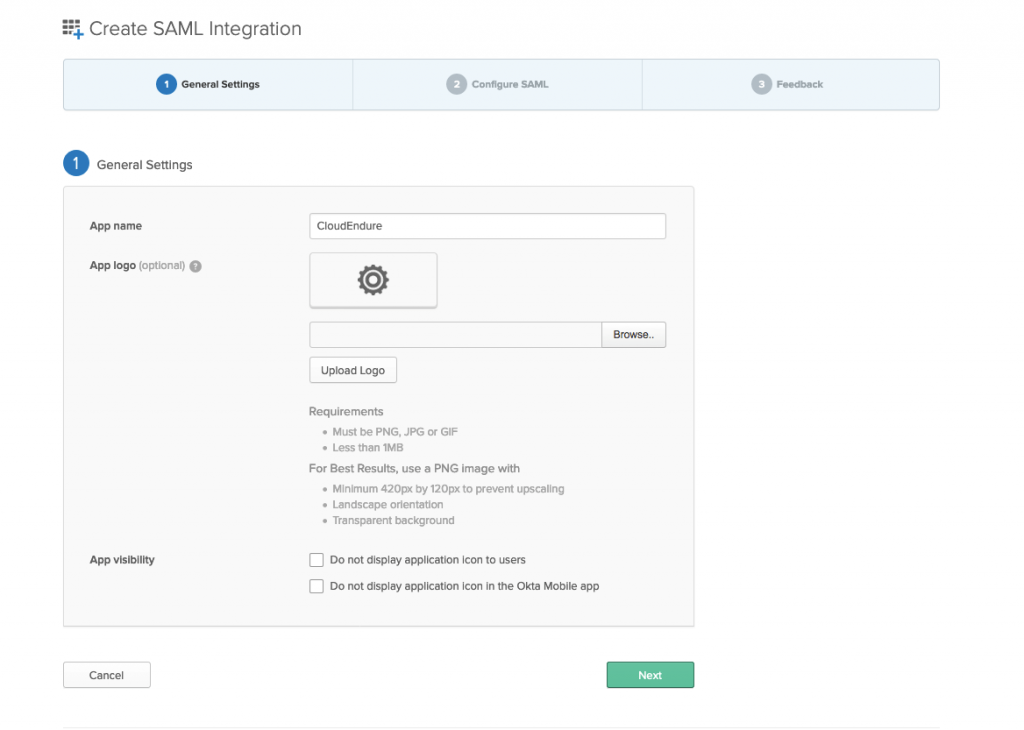
- For (1) General Settings, enter a name for the application. Keep the rest as default and select Next.
Note: I entered the name CloudEndure. If you have multiple CloudEndure accounts, one for DR and one for migration, you can create multiple applications. In that case, you may want to set the name that identifies the account so users know which account they are accessing.
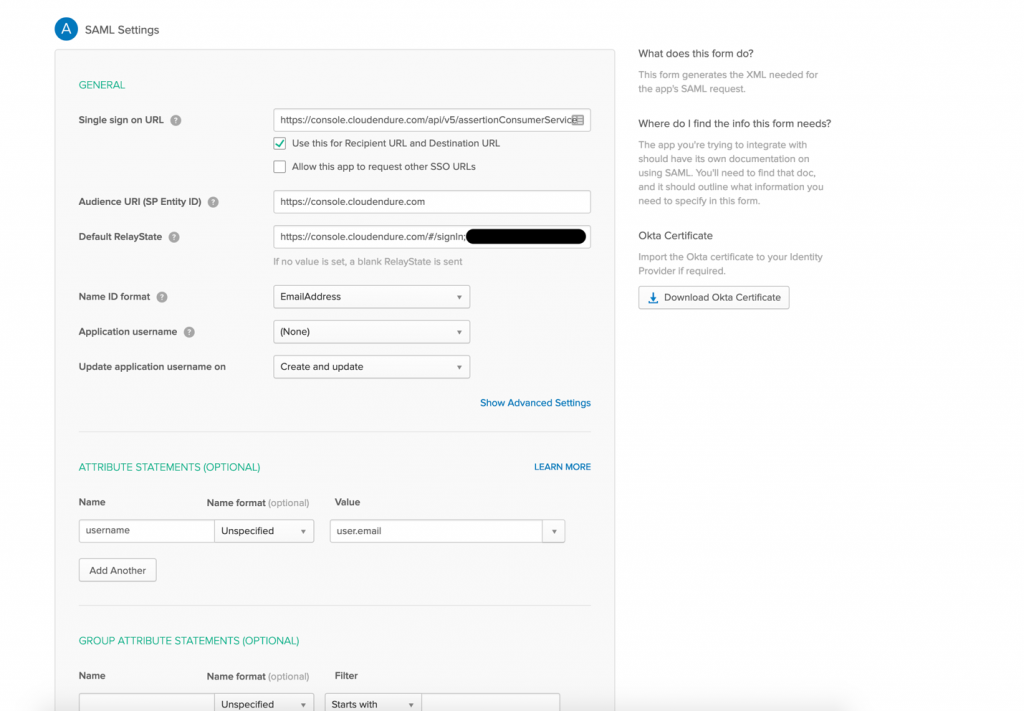
- In (2) Configure SAML, enter the following values, then select Next when complete.
- Single sign on URL: https://console.cloudendure.com/api/v5/assertionConsumerService
- Audience URL (SP Entity ID): https://console.cloudendure.com
- Default RelayState: https://console.cloudendure.com/#/signIn;<CE account UUID>
- Name ID format: EmailAddress
- Application Username: None
- Update application username on: Create and update.
- The following attributes are optional:
- Name: username
- Value: email
Note: See the subsection at the conclusion of this section for more information on getting your universally unique identifier (UUID).
- Complete Okta support (3) Feedback, then select Finish.
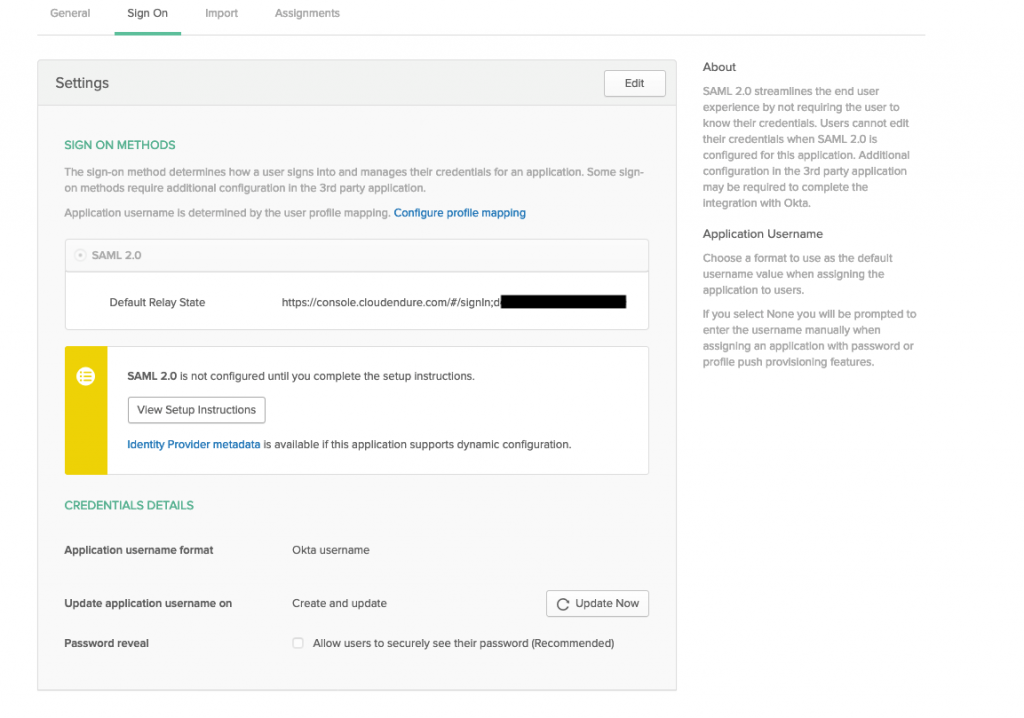
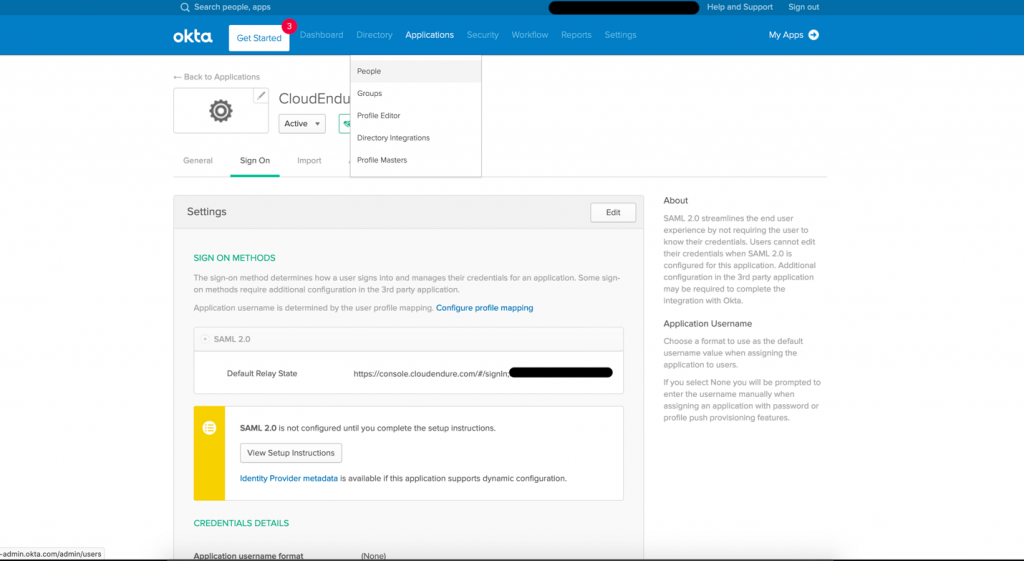
- You should now see the Sign On Methods. Select View Setup Instructions and you will see the Identity Provider Single Sign-On URL, Identity Provider Issuer, and X.509 Certificate. Copy them for the next section (Configuring CloudEndure Disaster Recovery).
Getting your account universally unique identifier (UUID)
Create the preceding relayState URL in a local text editor such as Notepad++ (UTF-8 encoding). Then copy it to the Okta settings to ensure that there are no special characters when pasting the account UUID. If this string does not have proper encoding, you may get “an error occurred during sign in” message with HTTP 500 error.
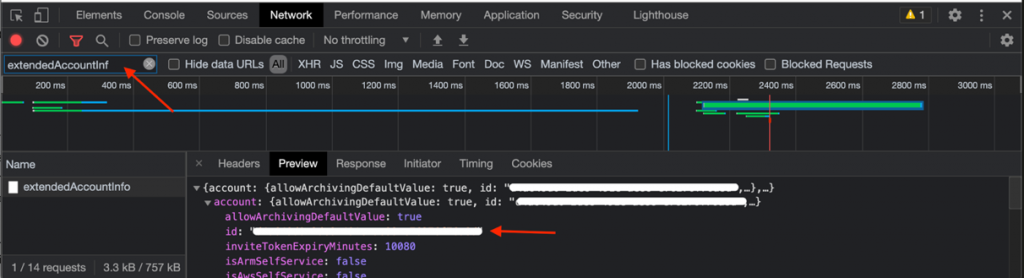
Get the CloudEndure Account UUID from the Developer Tools in your browser. From Chrome:
- Choose the Customize and Control Google Chrome (three vertical dots on right), then choose More Tools. Next, select Developer Tools and then the Network
- Log in to the account and check Extended Account Info
- Choose the field and choose the parameter: account and look for id, which is your Account UUID.
Configuring CloudEndure Disaster Recovery
In a separate browser tab or window, login to your CloudEndure account with an admin user.
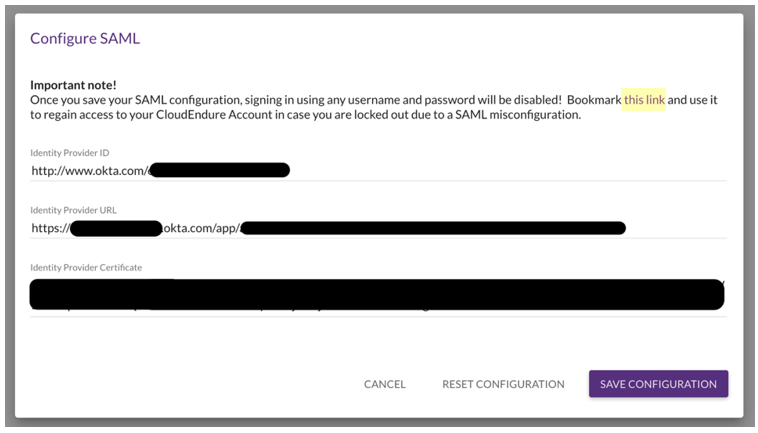
- On the top right, select the User Settings icon and choose Configure SAML.
- For this step, use the details obtained in step 8 of the preceding section (Configuring Okta). Use the Identity Provider Issuer from step 8 of the preceding section as the Identity Provider ID, the Identity Provider Single Sign-On URL as Identity Provider URL, and the X.509 Certificate as Identity Provider Certificate. Select Save Configuration when complete.
Important: As highlighted in the following screenshot, bookmark and save “this link” to regain access to the CloudEndure account to recover from SAML configuration errors.
Note: When entering the Identity Provider Certificate, download the X.509 Certificate or copy to a local text editor first and remove new line characters (the entire content should be one line). Then paste it in the CloudEndure console.
- Sign out of the CloudEndure console.
- Return to the Okta dashboard. Choose Directory and then People.
- Select on your user name and then choose Assign Applications.
- Assign the user name: <Enter email-id used for CloudEndure login> then Save and go back.
In order to use the SSO, the email address used to log into Okta should be a valid CloudEndure user. Creating the Okta account using [email protected] with the admin/owner user name for the CloudEndure user as [email protected] will result in an error. In that case, go to the Admin console in Okta > Directory > People > Add people. Create a user with the same address as the user name for CloudEndure. Then log out and log back into Okta as the new user.
In Okta, select My Apps on the right side and you’ll be taken to the home page with a button that reads CloudEndure. When you select this, you should be logged in into the CloudEndure account.
Congratulations! You have now successfully setup SAML-based SSO using Okta for CloudEndure Disaster Recovery.
Additional guidance
Since you are managing the users through Okta, you must add additional users so they are able to access CloudEndure. In this case, take the following steps.
- Add the user using unique email address in Okta.
-
- Go to Admin console in Okta. Choose Directory and then People. Choose the new user.
- Log in to the Admin account to go to CloudEndure console. Choose the User Settings icon, then select Manage users.
-
- Create user.
- Enter the email address of the new user you added to Okta. This should send an invitation link to your user.
- Assign CloudEndure App to the new user in Okta.
-
- Go to Admin console in Okta.
- Choose Directory and then People.
- Choose the new user.
- Assign Application and assign CloudEndure.
- Username: <user.email>.
- Save and go back.
Once the new user accepts the invitation, the user will be able to log in to CloudEndure from Okta.
Conclusion
In this post, we discussed how to set up an application and users in order to integrate CloudEndure Disaster Recovery into Okta SSO. Often a corporate requirement, SSO enables the streamlining access management and ensures compliance. By integrating CloudEndure Disaster Recovery with Okta SSO, you can improve the user experience and your organization’s security posture by maintaining the security and swiftness of SSO while also protecting your resources from disaster.
Visit the AWS CloudEndure Disaster Recovery product page or documentation to learn how to get started and to review customer case studies. If you have any comments or questions, feel free to share them in the comment section.